Parasite may reinstall itself multiple times if you don’t delete its core files. We recommend downloading SpyHunter to scan for malicious programs installed with it. This may save you hours and cut down your time to about 15 minutes.
Download SpyHunter Anti-Malware
More information on SpyHunter, steps to uninstall, EULA, Threat Assessment Criteria, and Privacy Policy.
Quick Access
Ok, so this article has been a long time coming.
One of my pastimes is reverse engineering Android applications, just to see “what makes them tick”. In this article, in order to really drive this home, I will reverse engineer the popular “Angry Birds” application.
Due to time constraints and basic laziness, I went for the first APK I could find – Angry Birds in Space.
Also, before anyone asks, in the following article I will NOT be releasing the Angry Birds source code. I simply am using it as a demo ![]()
First off, you will want to have the Unix “unzip” utility installed. We will be using this to unpack the .apk file.
Second, grab the following pieces of software:
dex2jar – http://code.google.com/p/dex2jar/ – for converting the .dex file into a .jar file ![]()
and
jd-gui – http://java.decompiler.free.fr/?q=jdgui – For decompiling the (.jar) Java file into its (.java) source code ![]()
Now, the idea behind this article is NOT to teach you to crack apps. Instead, this is the skillset needed to reverse engineer Android Malware – as seen in my previous post – http://insecurety.net/?p=637
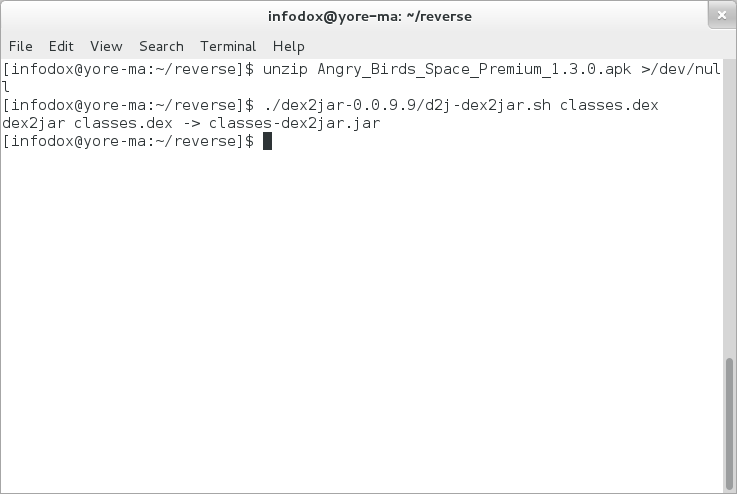
So. You have your .apk file, the first thing we do is use the GNU Unzip utility to unpackage it!
$ unzip Angry_Birds_Space_Premium_1.3.0.apk
Next, use the d2j-dex2jar.sh utility from dex2jar to convert classes.dex to a JAR file.
$ ./dex2jar-0.0.9.9/d2j-dex2jar.sh classes.dex
Screenshot of the above 2 steps (I piped output to /dev/null to avoid MASSIVE SPAM OF DATA)
 unzip and dex2jar
unzip and dex2jar
Next, we simply open the .JAR file using jd-gui.
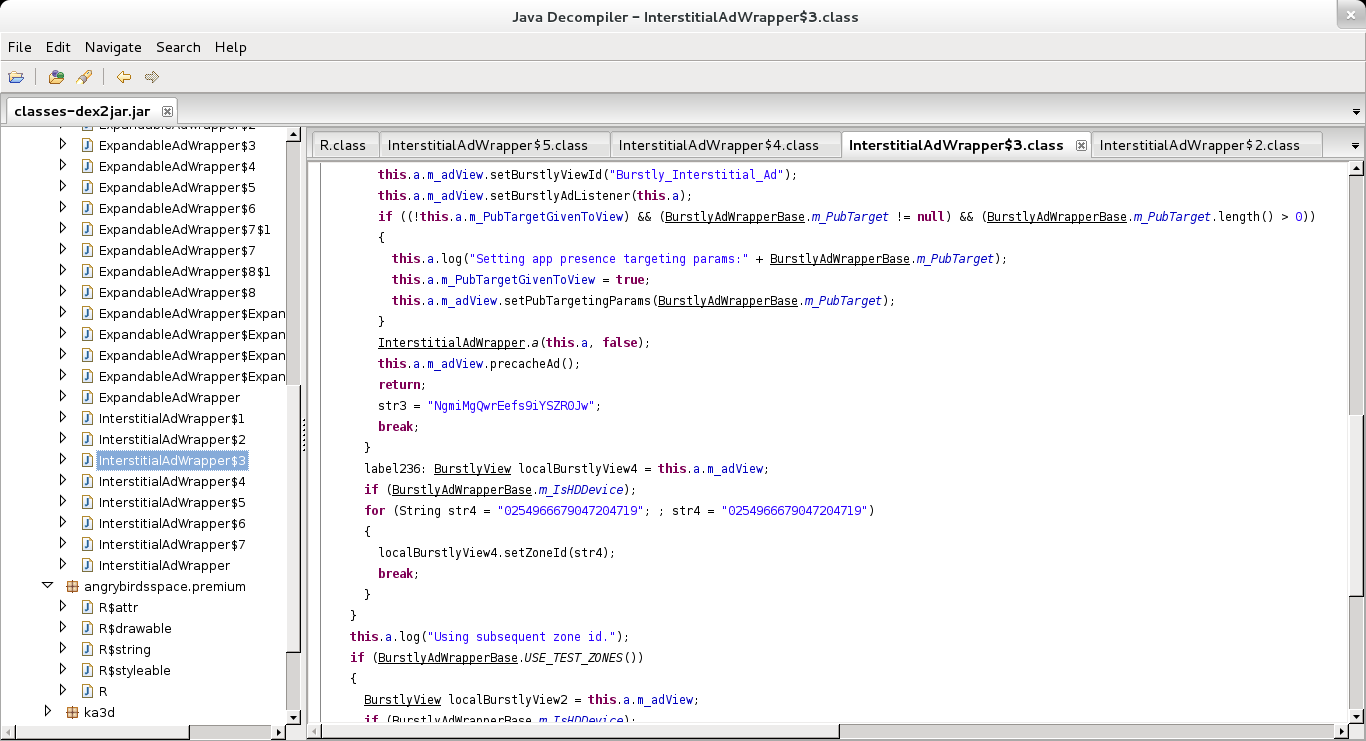 Decompiling the JAR file
Decompiling the JAR file
Finally we can simply export the source code from jd-gui for our viewing, and editing pleasure ![]()
So. In conclusion
- Android applications are trivial to reverse engineer
- Software for decompiling them is readily available
- Fun times


Leave a Comment